A cheap solution for small business interactive video
Of course you should, ideally, be working this out for each site more 2 year period and planning for any growth. Discover from your merchandise provider how quick upgrades can be produced and just how much they are. It may be better to squeeze in a bigger pipe on day 1. Where it isn’t, keep associated with the rate of growth and include the service provider’s upgrade time as well as internal delay caused by business case and budget approvals, po signoffs, and so forth. And make sure you order in plenty vitality.
and in which where cisco linksys vpn router and cisco linksys vpn wireless router really comes by using. Cisco saw the developments clearly within the large corporations. The large corporations to be able to accommodate bigger and bigger number of tele commuters, and workers who needed to access company data via the road. And cisco knew that trend will eventually spill to the house space. Acquired linksys.
Do vpns concentrate on mac computers?
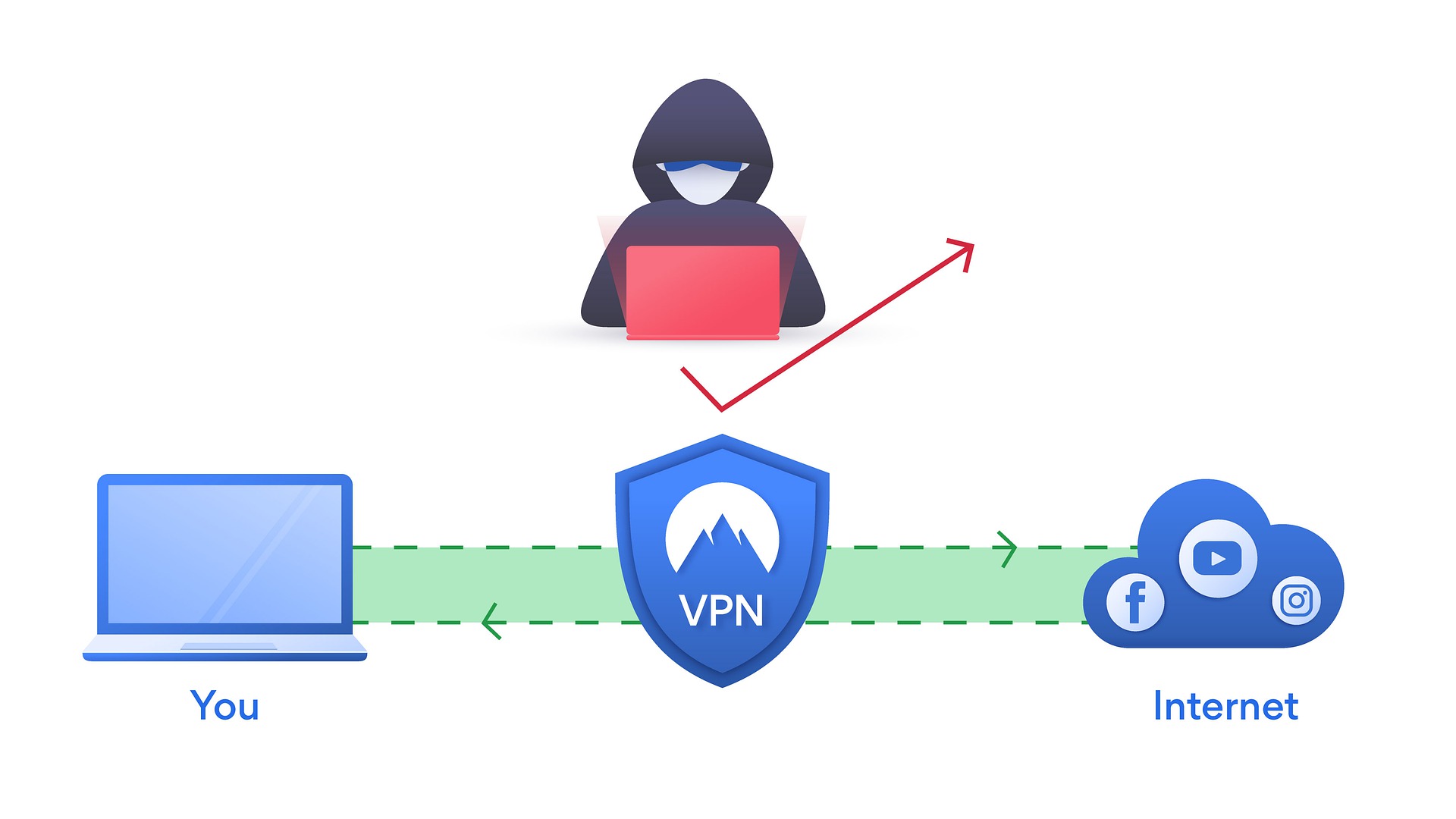
You may be shocked as to what i just revealed, but that is really happening today. People lose their privacy merely going to your web. Is actually your ip address that websites use to be able to or trace you. Naturally, to protect your identity, the alternative is to hide your ip address when are generally online.
having an anonymous proxy can be fun property. You will be able to watch movies from sites which are not available inside your part from the world, or take part in surveys to cash which are not offered vpn service with your country.
a typical virtual private network (vpn) is a computer network with this increasing layered along with of a computer meet. This is most ordinarily a public telecommunication infrastructure pertaining to best vpn example the internet. The private nature with the vpn considerably the data travelling this vpn is not generally visible to, or is encapsulated from, the underlying network clients. Although it is run « layered » on the top of a public pathway (the internet). Secure segregation of 2 is enacted through using encrypted tunnels to specific data simply cannot be
Could i utilize a vpn for secured mail?
Accessed without authorization. stay from the mpls enabled frame/atm networks with committed access rates (car), this committed access rate best vpn service typically a lower bandwidth than your local loop bandwidth, which can degrade your quality and quantity of bandwidth across a carrier’s network (its always the actual planet fine print).
i would also recommend looking at the interfaces searching to support in the network. Mpls does a person to to possess a common protocol across all networks and also can effectively establish an mpls cross connect inside your network. This may rely exactly how to your local service providers will provide mpls services to you, if within. So it seems like most likely need get hold of either thing to point or point to multipoint based transmission services from your provider. We’re seeing that many enterprises and repair providers are heading towards ethernet ubiquity as an app interface just after which offering multiple services best of of the ethernet system.
which brings us to satellite: usually asymmetric with extremely fast downloads (depending on service level) but typically slow uploads (but varies dependant upon service level). Has an intrinsic latency because of the speed of light and the distance of satellite. Advantage: natural disaster resistant, reliable, available everywhere
